The understanding of Public-Key-Infrastructures (PKI) is crucial for anyone who wants to ensure secure communication in networks. PKI plays a central role in the creation, distribution, and validation of digital certificates. These guidelines help to establish a robust system that ensures that communication between users and servers is protected.
Key insights PKI enables the authentication of public keys, signing and encrypting messages, and provides a secure method to confirm digital identities. This is done through digital certificates issued by a Certification Authority (CA) that verify the authenticity of public keys.
Step-by-step guide
1. What is PKI?
Before diving into implementation, it is important to understand the basics. PKI is a set of roles, policies, hardware, software, and procedures necessary to issue, distribute, and verify digital certificates. This infrastructure enables the securing of computer-assisted communication by using solid asymmetric cryptosystems.

2. The role of digital certificates
Within PKI, you will find that digital certificates are essential components. They serve to confirm the authenticity of a public key and define its legitimate uses. A digital certificate is secured by a digital signature that can be verified with the public key of the Certification Authority.
3. The certificate exchange process
To ensure the secure transmission of messages, the sender needs the public key of the recipient. This key can be sent via email or downloaded from a secure webpage, for example. It is important that the integrity of the key is maintained during this process. That's why PKI plays a crucial role at this stage.
4. The Certification Authority (CA)
The CA is the heart of any PKI. It is responsible for creating and signing digital certificates. For example, when Anna sends a message to Peter, she receives a certificate from the Registration Authority that can be verified by the CA. The CA plays a trusted role in the PKI, as it ensures that the issued certificates are reliable and authentic.
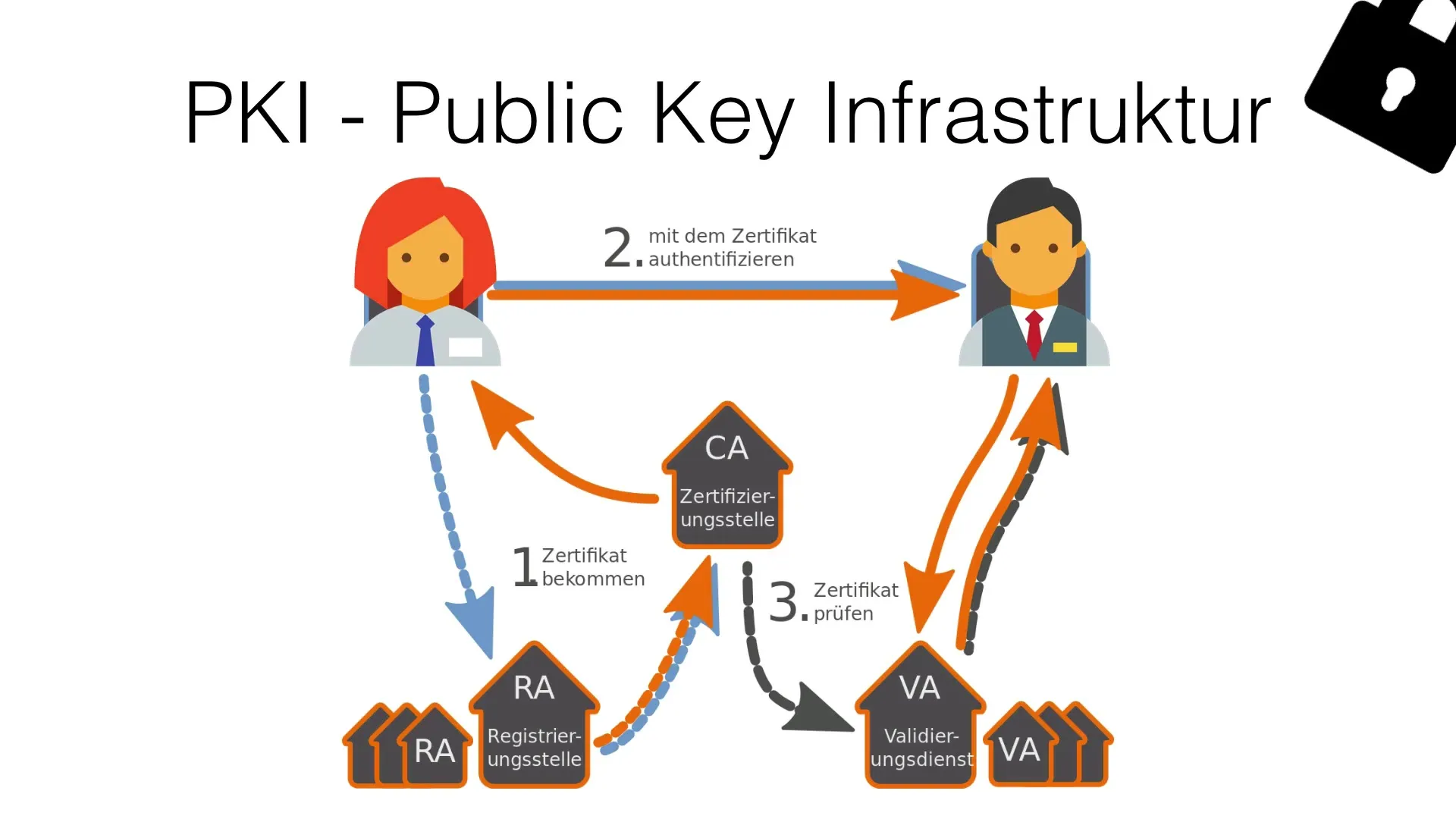
5. Validation service
A validation service checks the validity of certificates. Before Peter decrypts the message from Anna, he should ensure that the certificate is genuine and the document is uncompromised. The validation service connected to the CA performs this check so that Peter can be sure that the message actually comes from Anna.
6. Certificates and key types
Within the PKI system, you will use different types of certificates and keys. For example, there are certificates for clients and servers, with each key needing to meet specific security requirements. The client and server keys must be stored in the appropriate places to ensure optimal protection.
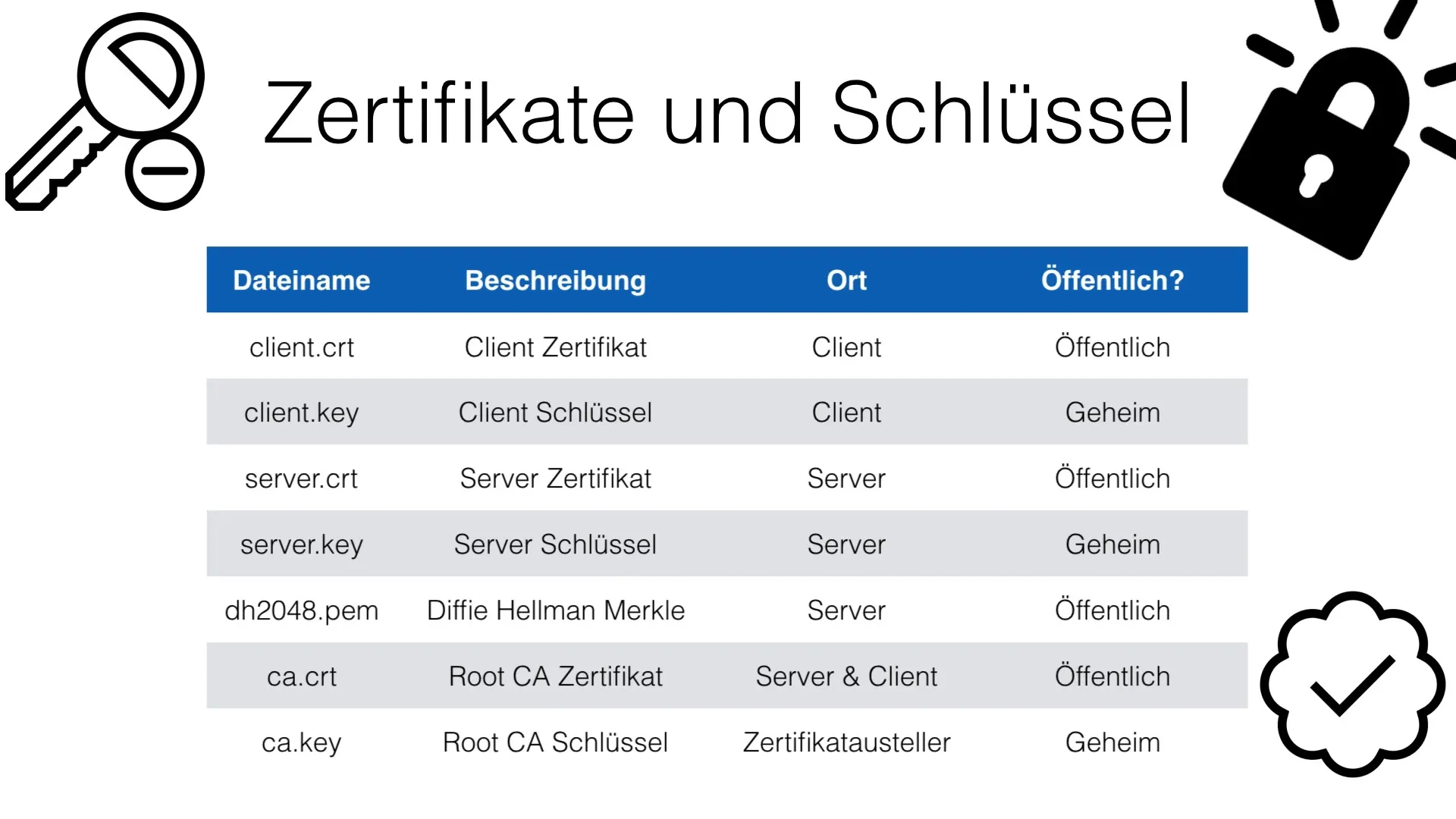
7. Confidentiality and public keys
When handling keys, it is important to distinguish between public and private key files. The client key should be kept confidential, while the server certificate can be public. The root certificate, on the other hand, remains private and is managed by the certificate issuer (CA).
8. PKI in practical use
When setting up your OpenVPN server, it will help that OpenVPN already brings the necessary tools to efficiently generate certificates and keys. While the implementation requires some technical steps, with the right instructions, the process will be significantly easier.
9. Outlook on the next lesson
Now that you have a solid understanding of PKI and its components, you will dive into the topics of bridging and routing in the next chapter. These concepts are essential for further securing your network and optimizing the performance of your connection.
Summary – Understanding and setting up PKI: Public-Key Infrastructure
In this guide, you have learned what a Public-Key Infrastructure is, how digital certificates are created and validated, and why these elements are important for secure communication. The establishment of PKI not only provides security but also trust in digital identities.
Frequently asked questions
What is a Public-Key Infrastructure (PKI)?PKI is a system for managing digital certificates that enables their creation, distribution, and validation.
What are digital certificates?Digital certificates confirm the authenticity of a public key and define its allowed uses.
How does the validation of a certificate work?A validation service checks the validity of a certificate to ensure that it was issued by a trusted CA.
What are the main components of a PKI?The main components are digital certificates, Certification Authority (CA), public and private keys, as well as validation services.
How is a public key certificate exchanged?A public key can be sent via email or downloaded from a secure webpage, while maintaining integrity.


