The importance of secure communication over networks often becomes clear only in moments when security actually matters. OpenVPN allows you to create encrypted connections that protect your data from prying eyes. In the following, you will learn how to generate user-keys, which are essential for authenticating your clients.
Key insights User keys are necessary to securely authenticate clients in the OpenVPN network. By creating key pairs, each client receives its individual access credentials. This not only enhances security but also simplifies the management of your users.
Step-by-Step Guide
First, ensure that you have access to the OpenVPN directory. Typically, you will find this in the OpenVPN installation folder under the /easy-rsa directory. To create user keys, you need to follow a few basic steps.
Now you will load the vars script, which provides you with the necessary environment variables. This is done by executing the following command in your terminal:
If you later want to create another client, it is crucial not to skip this step. The command source vars ensures that all variables for certificate creation are loaded correctly.
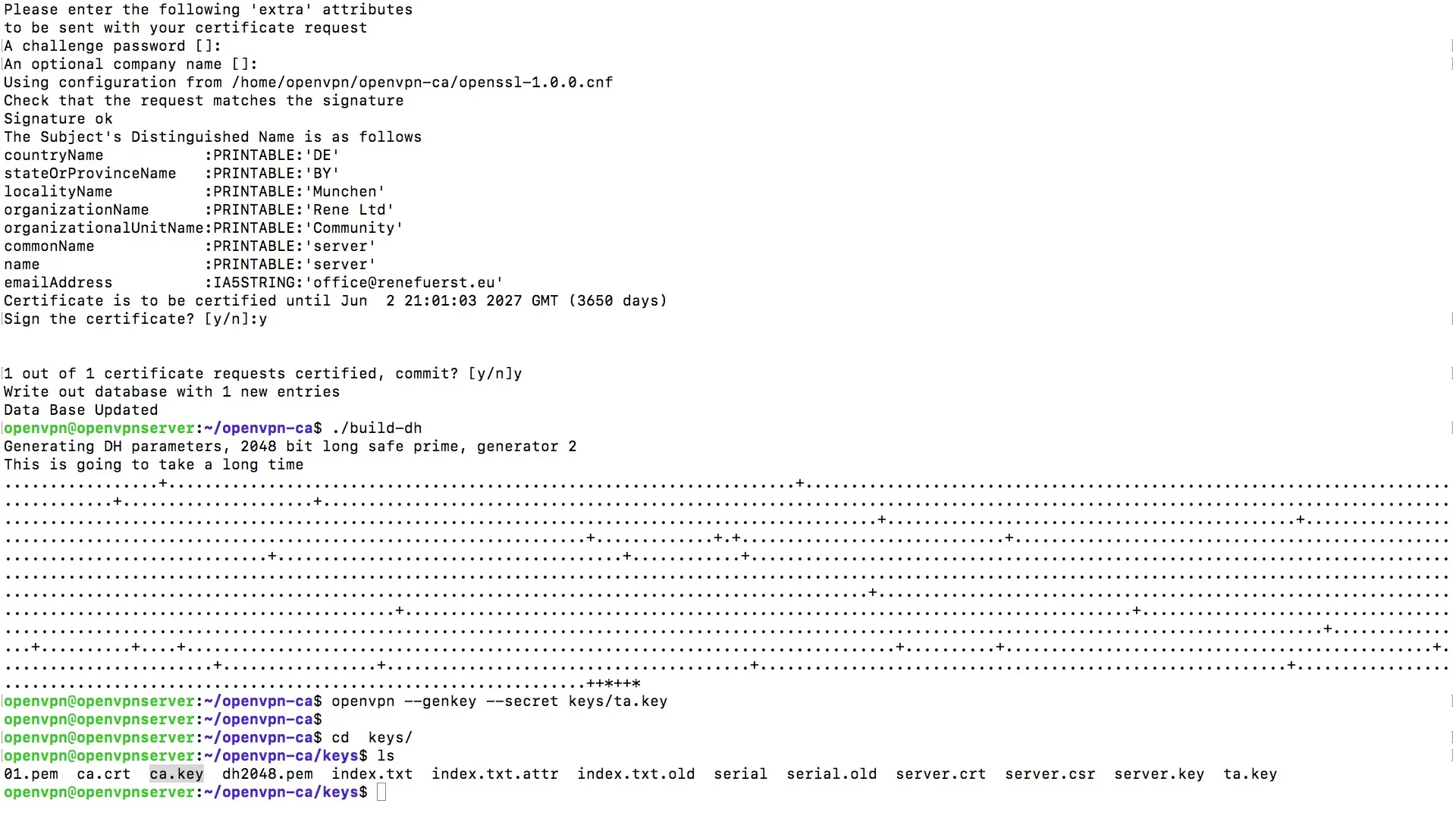
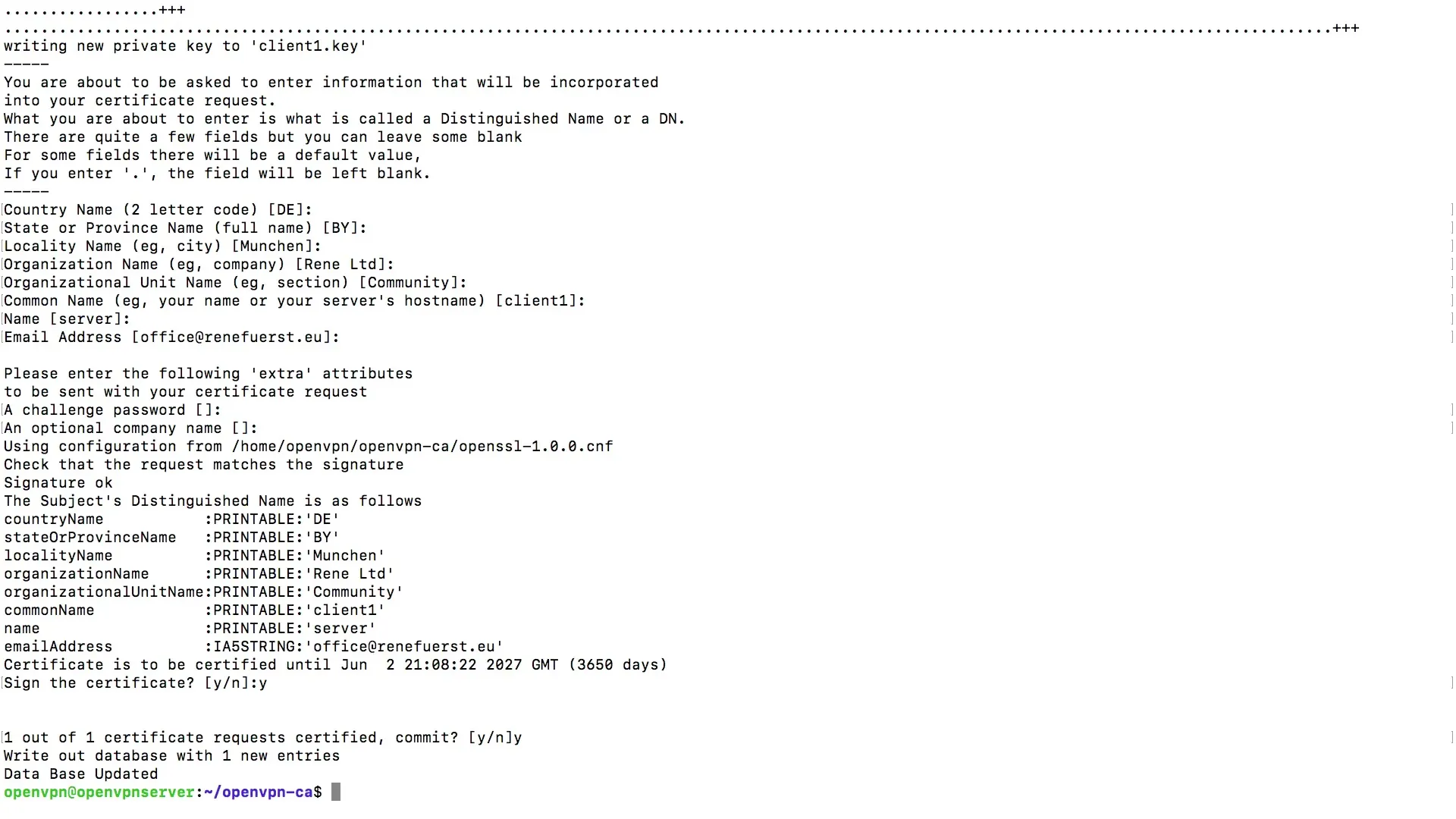
In the next phase, you will create the actual key for your first user. To do this, enter the command to create a key and assign a name for the client, for example Client 1.
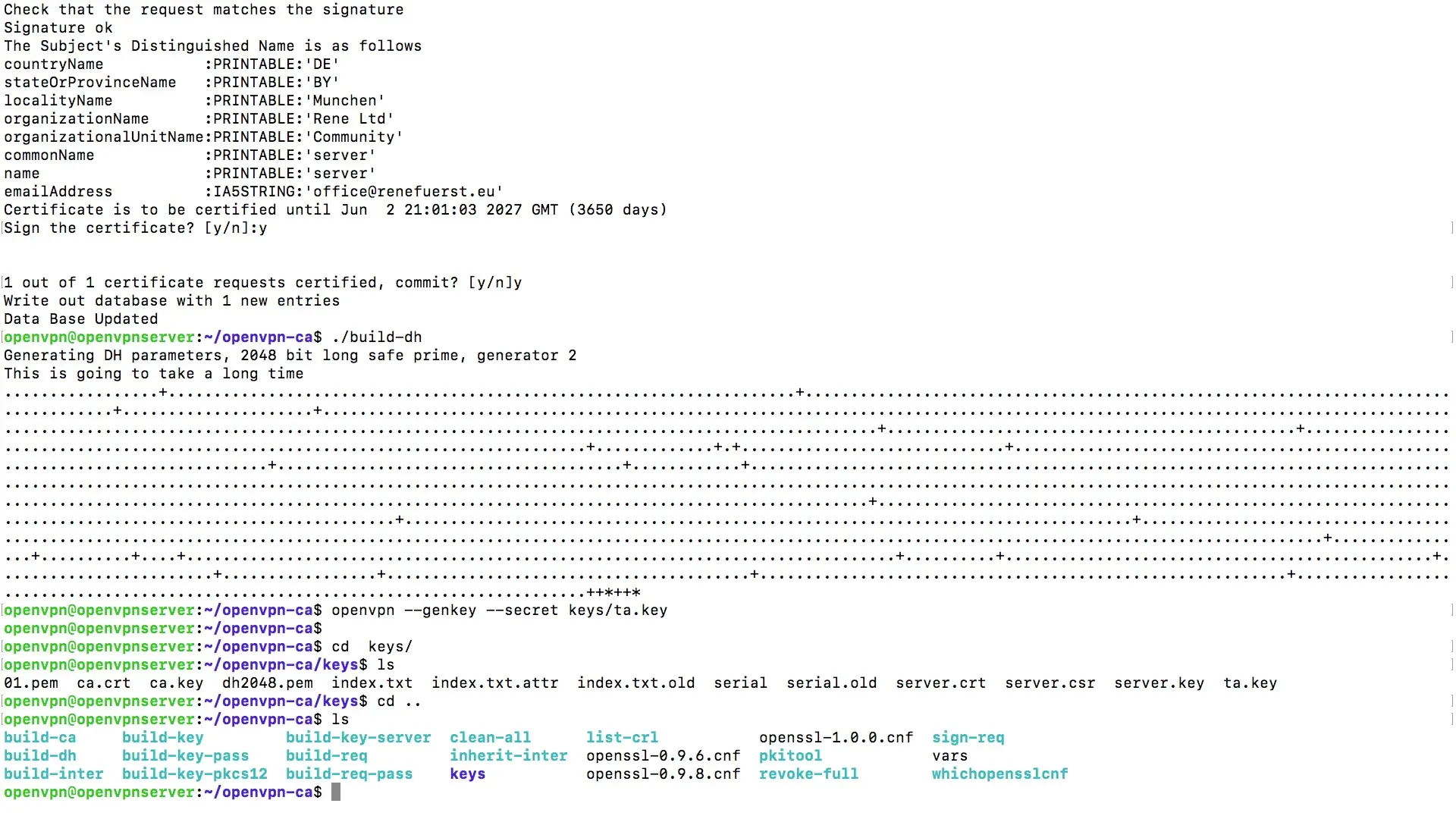
The console will prompt you to provide some information. Here, you enter the hostname, which in this case is Client 1. When prompted for the name, you can simply enter Server. It is crucial that you do not enter a password if you want to authenticate solely with the keys and certificates.
After entering this information, you will see that a new entry has been written to the database. These entries are important for managing the authentication of the clients.
If you later want to delete a client, it is necessary to revoke the corresponding permissions so that the client can no longer log in with the generated key.
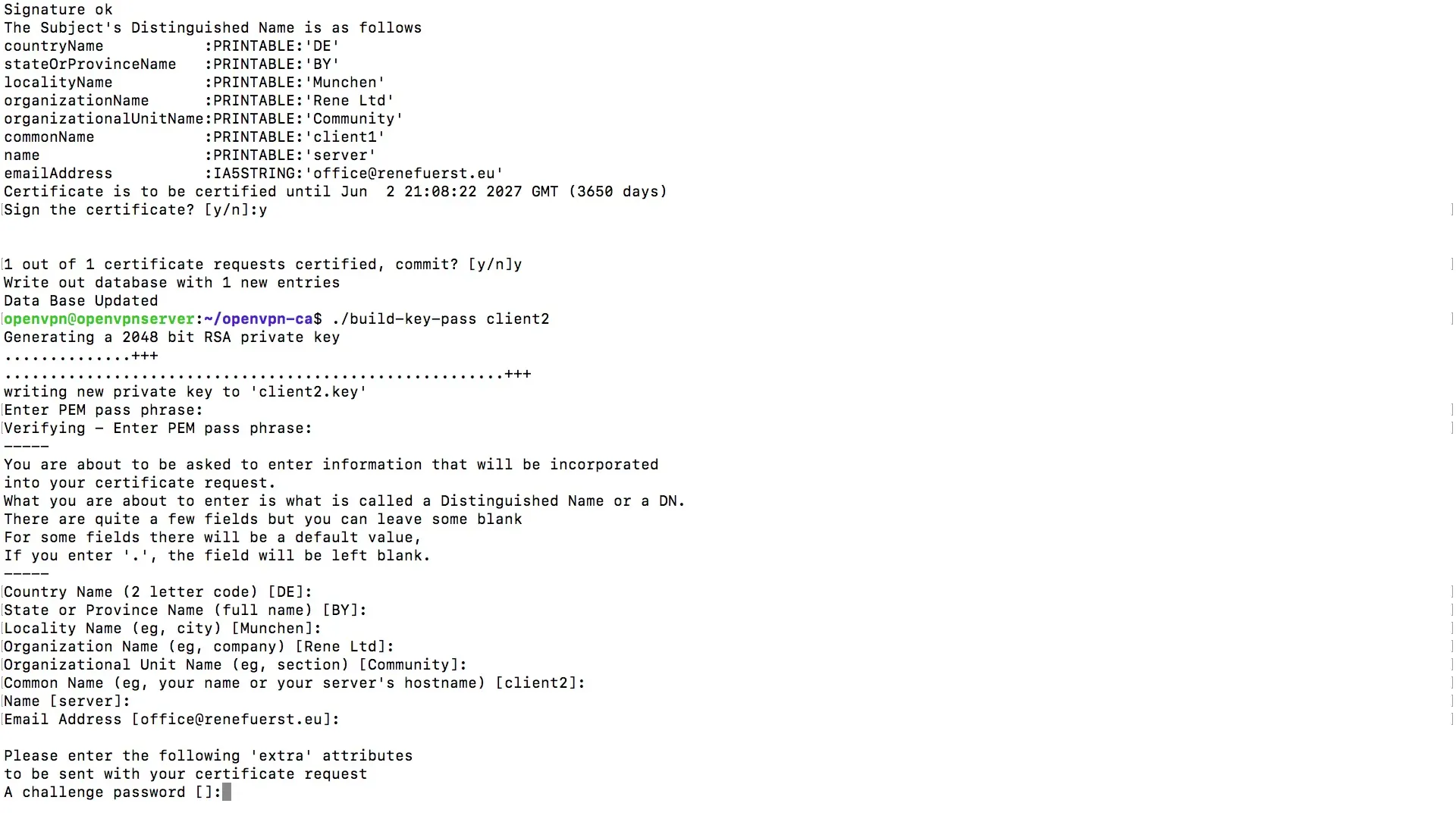
However, if you want to create a password for additional security, you need to use the command for creating a password-protected key instead of the simple key. This is done in a similar manner, but now you need to enter a passphrase.
You will be prompted to create and verify the passphrase. The passphrase increases the security of the connection and provides additional protection.
After successful entries, a second entry will be created in the database, and you now have a way to create user keys with password protection.
In summary, you can create specific key pair certificates for each client. The files for each client are stored in the keys folder, and you can also name the clients after usernames, which improves clarity.
The actual files you will receive include.crt,.csr, and.key files for Client 1 as well as for each additional client you add.
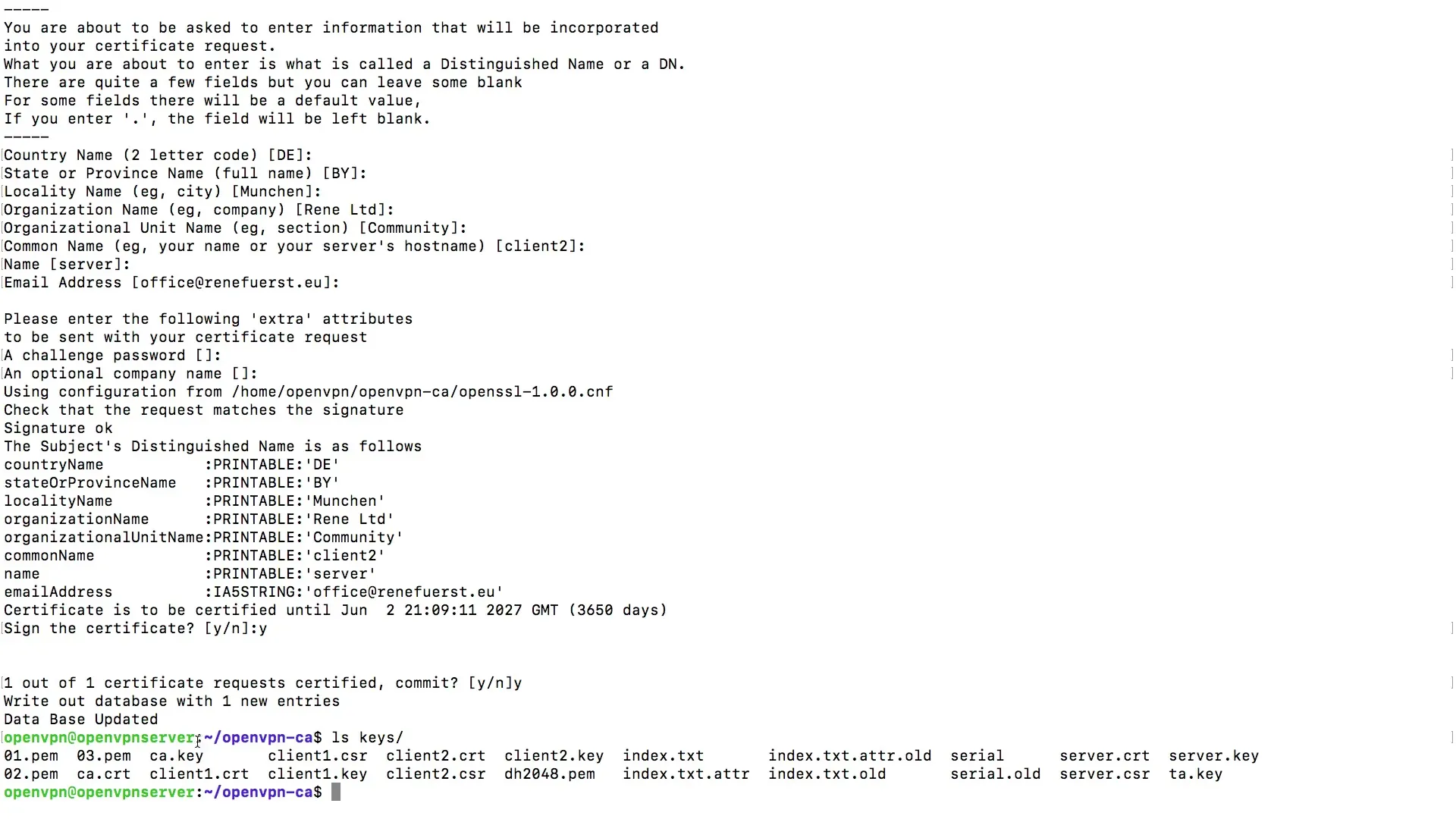
With this, you have successfully created small certificates with key pairs. This foundation enables you to proceed with the configuration of the OpenVPN service in the next phase.
Summary – OpenVPN: Creating and Configuring User Keys
Throughout this guide, you have learned how to effectively generate user keys to securely authenticate clients in the OpenVPN network. By individually generating key pairs, each client receives its personal access, significantly enhancing the security and management of your users.
Frequently Asked Questions
How do I create a user key for OpenVPN?You need to load the vars script and then execute the command to create the key for the desired client.
Why should I use a password for my key?A password for your key provides additional protection and increases the security of your connection.
How do I manage multiple clients in OpenVPN?You can create an individual key pair for each client and name them after usernames.
Can I delete a client afterwards?Yes, you can delete a client, but you must revoke permissions so that it can no longer log in with the key.


